Cyber attacks have posed real threats and devastating impacts on individuals and enterprises. People from all walks of life have been the victims of cyber attacks. When discussing a secure environment, we consider cyberspace, including everyone with a digital presence.
The blog outlines 5 actionable tips we, as individuals and corporations, can use to mitigate the risks of cyber attacks.
How do you prevent cyber attacks?
Cyber attacks have evolved with time. Some intruders have grown technologically, while others have changed their tactics. For each episode, countermeasures differ, but there are some general tips you must follow:
1. Technical Security Controls
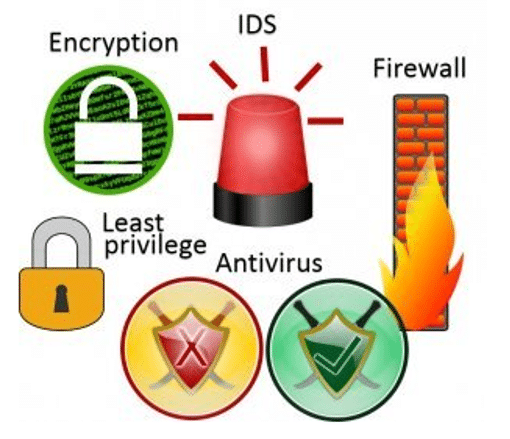
The logic controls, which include: encryption, firewall, intrusion systems, use of anti-virus and VPN, are the basics. These tools are readily available and are easy to use for each one of us.
a. Administrative Security Controls
This refers to the administrative policy of the organizations. Clear guidelines about the security posture must be maintained at all levels with resilience. To implement the administrative controls, other management and operational tools are to be implemented.
b. Physical Controls
These controls ensure that unauthorized access is prevented. Tools such as biometrics, 2FAs, and surveillance cameras can be used.
c. Preventive and Detective Controls
This includes training and education and the use of technology to analyze the threats. The tools used can be Log monitoring, SIEM, Trend Analysis, and security audits.
2. Vulnerability Management
Vulnerability management refers to the idea of identifying all risks, and discovering weaknesses and vulnerabilities across all the assets. This doesn’t only conform to companies but to individuals too. Some types of vulnerability assessments include:
- External scans
- Internal scans
- Network assessment
- Host-based assessment
- Wireless and database assessments
- Web-application assessments
Vulnerability assessments prove to be on-point when mitigating the cyber security risks. The quantifiable metrics it provides are the concrete remedy to patch the potential dangers.
3. Endpoint Detection and Response
The endpoint is the communication corners through which communication initiates or stops. Commonly referred to as our devices. When we talk about endpoint detection and response, we refer to the technology that checks the communications these endpoints make to have higher visibility about the data being compromised.
What can EDR do?
- Can provide statistics about how the attacker gained access to the system and what they did.
- Can detect malicious activity on an endpoint due to zero-day exploits, advanced persistent threats, fileless or malware-free attacks, which don’t leave signatures and can, therefore, evade legacy anti-virus.
4. Investing in Next-Generation Firewalls (NGFW)
Firewalls are only associated with network traffic that is based on the IP address, and port number of the packets delivered. With NGFW, you can get your dynamic packets filtered, which means the process of determining access is thoroughly monitored.
According to Fortinet: “Next-generation firewalls (NGFWs) have evolved significantly from their early days when they relied only on the appearance of network traffic. Now, they need to protect all parts of a business and can do far more, such as filtering Layer 7 applications, blocking harmful attachments and links, detecting known threats and device vulnerabilities, deploying patches, preventing DDoS attacks, and offering web filtering for direct internet access”.
Firewall Penetration Test
Firewall penetration testing involves finding, exploring, and breaching a specific firewall to access the trusted internal network of a particular system. It is commonly regarded as a crucial aspect of external network penetration testing, and firewall testing is highly significant as firewalls serve as the initial barrier against external attacks.
5. Data Loss Prevention Strategy
Data loss prevention (DLP) strategies refer to measures and techniques implemented to safeguard sensitive information from being lost, stolen, or compromised. These strategies mainly focus on preventing unauthorized access, accidental disclosure, or intentional data leakage. The technique is equally important to individuals and organizations with planning differences.
- Data assorting: To categorize data based on its sensitivity level and apply appropriate security controls and protections accordingly.
- Access controls: To implement strict access controls to authorized personnel only. This involves user authentication, role-based access control (RBAC), and least privilege principles.
- Encryption: To utilize selective encryption techniques to convert data into unreadable formats, making it unintelligible to unauthorized individuals even if they gain access.
- Awareness and training: To educate employees about data security best practices, potential risks, and their responsibilities in handling sensitive information.
- Data Backup and disaster recovery: To implement regular data backups and establish robust disaster recovery plans to ensure that data can be restored in case of accidental loss, system failures, or cyberattacks.
- Data leakage prevention: To employ technologies and policies to monitor and prevent the unauthorized transmission of sensitive data outside the organization’s network or designated boundaries.
- Data retention and disposal: To establish guidelines for retaining data for the required duration and implementing secure data disposal practices to ensure that sensitive information is properly destroyed when no longer needed.
- Regular auditing and monitoring: To conduct periodic audits, vulnerability assessments, and real-time monitoring to identify potential security gaps, detect anomalous activities, and promptly respond to security incidents.
Carpe diem
Cyber criminals and their tactics come in various colors and shapes. It is only us who can counter them with our vigilance and proactive approach. The network, wireless, social engineering and malware attacks are prevalent.
Today, it is not important to know why these attacks occur, but to know how to mitigate them and fight them back.