Cyberattacks and malware are a constant concern for individuals and organizations alike. To effectively combat such threats, malware analysts investigate them to ensure proper defense. Here are five types of software they regularly utilize in their work.
1. Sample Repositories
Malware sample repositories are online collections of malicious software specimens that are utilized by cybersecurity professionals, researchers, and organizations. These repositories serve as a resource for studying and analyzing the behavior of malware to improve detection and evaluate the effectiveness of security solutions.
Here is why malware repositories are important:
- A large and diverse collection of malware samples is available for comprehensive research and analysis.
- Security experts can use the samples to create more precise and effective malware detection tools.
- Organizations can test their security solutions to identify and fix vulnerabilities or weaknesses.
By using malware sample repositories, security professionals can gain a better understanding of the latest malware threats and improve their organization’s overall security posture.
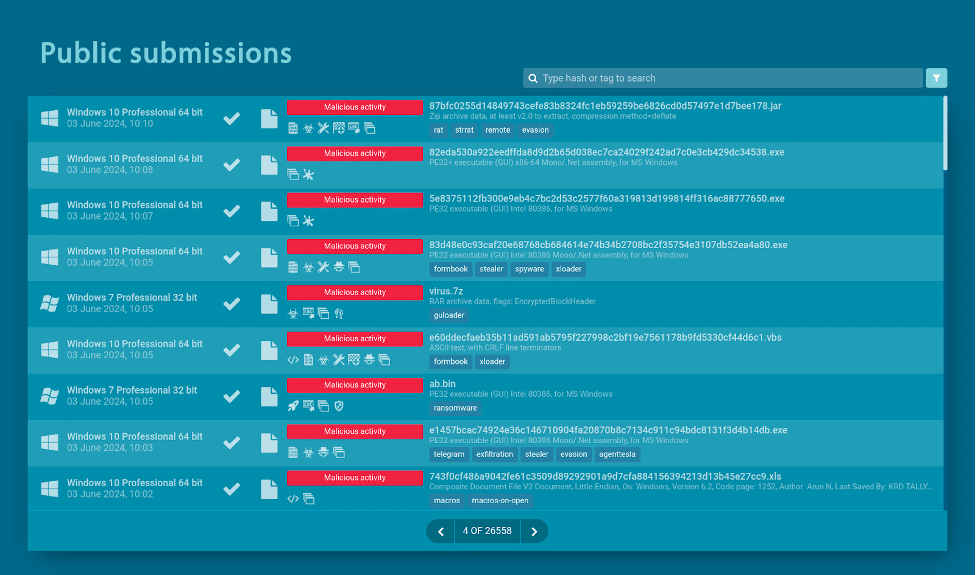
ANY.RUN’s public submissions database
A good example of one such repository is ANY.RUN’s public database of malware samples. It is a service that contains millions of sandbox sessions launched by the users of the ANY.RUN malware sandbox.
As a result, you can not only download a sample of any malware, but also view a detailed analysis report, including a video recording of the entire sandbox session.
| Sign up for a free ANY.RUN account to analyze latest threats! |
2. Malware Sandbox
A sandbox is a controlled environment where potentially harmful software can be executed and analyzed without posing a risk to the larger system or network. It is extensively used by analysts to study the behavior of malware, test software for vulnerabilities, and develop effective security solutions.
ANY.RUN’s cloud sandbox combines a number of essential malware analysis tools that significantly streamline the process of analyzing malware for users, as it:
- Detects any threat present in a file or URL in under 40 seconds.
- Shows malware’s network traffic, registry and file activity, and all processes launched during the analysis session, as well as highlights malicious behavior.
- Maps the malware’s tactics, techniques, and procedures (TTPs) to the MITRE ATT&CK matrix.
- Provides detailed threat reports that contain indicators of compromise (IOCs) and malware’s configurations.
One of the standout features of ANY.RUN is interactivity. The service lets you engage with the virtual machine and control it just like a standard computer. Users can open documents, browse the internet, download files, and even reboot the system.
It is an extremely useful feature for analyzing threats that require human interaction, such as phishing emails with links and attachments, including password-protected archives.
Here is an example of a phishing email analyzed in the ANY.RUN sandbox.
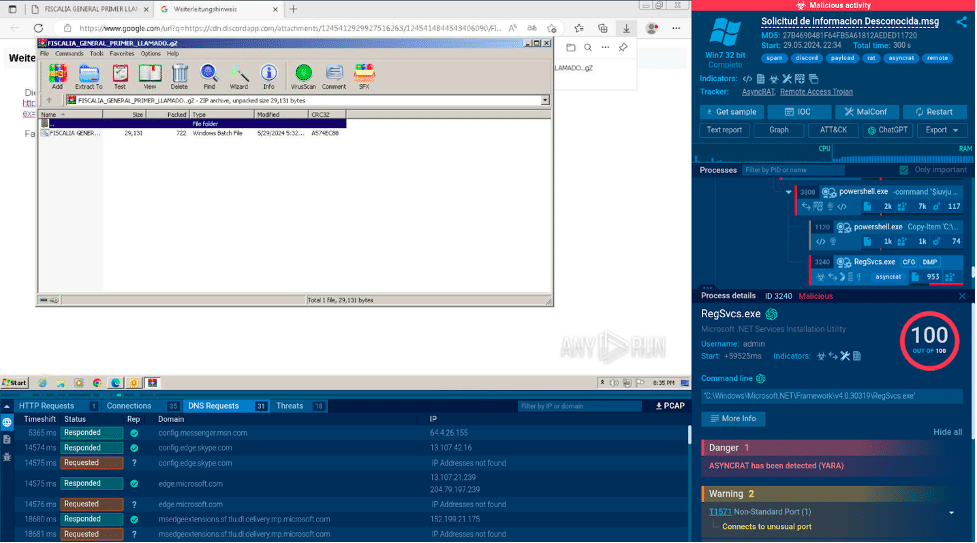
The phishing email containing an Asyncrat sample analyzed in ANY.RUN
The user gets to open the email in the sandbox and follow through with each step of the attack, including a phishing page and a malicious archive which contains an Asyncrat malware executable.
| Sign up for a free ANY.RUN account to analyze files and links with no limits! |
3. Packer Identifier
A packer is a tool used by malware authors to compress and obfuscate their malicious code, making it more difficult for security solutions to detect and analyze. Packer identifier software works by analyzing the binary structure, headers, and other characteristics of an executable file to determine if it has been packed and, if so, which packer was used. Some packer identifier tools can also unpack the executable, restoring it to its original state for further analysis.
- Here is why packer identifiers are important:
- It helps identify executable files that have been packed to evade antivirus software.
- By identifying the packer used, security teams can gain insights into the tactics and techniques used by malware authors.
- It makes it easier for analysts to focus on more complex aspects of reverse engineering.
4. Debugger
Debugger software is a tool used in software development and reverse engineering to analyze the behavior of an executable file at the code level. It allows developers and analysts to step through the code, set breakpoints, inspect variables and memory, and more.
Here is why debuggers are important:
- They help analysts understand how the malware operates, identify indicators of compromise, and develop effective detection and mitigation strategies.
- Such software lets professionals bypass evasion techniques used by malware.
By using a debugger, developers and cybersecurity professionals can carry out all the essential reverse engineering operations.
5. Disassembler
A disassembler is another type of software utilized in reverse engineering. It converts machine code into assembly language. This conversion allows analysts to understand the low-level functionality of an executable file, including the instructions that are executed by the CPU and the interactions between different components of the system.
Here is why disassemblers are important:
- Disassemblers are essential for static analysis, as they allow analysts to examine the code of a malware sample without executing it.
- They make it possible to study samples at a granular level, including the individual instructions that are executed by the CPU.
- Disassemblers enable analysts to identify and reverse-engineer obfuscated code.
Conclusion
Analyzing cyber threats is critical for organizations to protect their networks and data from potential attacks. The tools mentioned in this article, including malware sandboxes, packer identifiers, debuggers, and reverse engineering software, can help security analysts identify and mitigate potential threats more effectively.
