Authored by Amal Mammadov, Information Security Manager and reviewed by the Metapress editorial team, this article was published following a careful evaluation process to ensure quality, relevance, and editorial standards.
After hearing that a colleague had fallen for the same fraudulent delivery scheme I uncovered a few years ago, I decided to make my original findings more accessible to a global audience by translating them. The original Russian version remains available for reference.
The Setup: A Seemingly Innocent Inquiry
It started when I listed a children’s table for sale on a local marketplace called Kufar.by. Two days later, I received a message via Viber from a Ukrainian phone number. The sender, identifying herself as Margarita, expressed interest in purchasing the table. After a brief exchange about the item’s condition, she proposed using a courier service—specifically CDEK, a well-known logistics company in Belarus and Russia—to complete the transaction.
I admitted my lack of familiarity with courier shipments. Margarita offered to guide me through the process, even sharing a screenshot from the supposed CDEK website. She explained that the payment would be securely held by CDEK until the item was delivered—positioning CDEK as a trusted third party.
To simplify things, she offered to fill out the delivery form on my behalf and requested my full name and address. She then claimed to have completed the payment and shared a link to a website, which appeared professional at first glance.
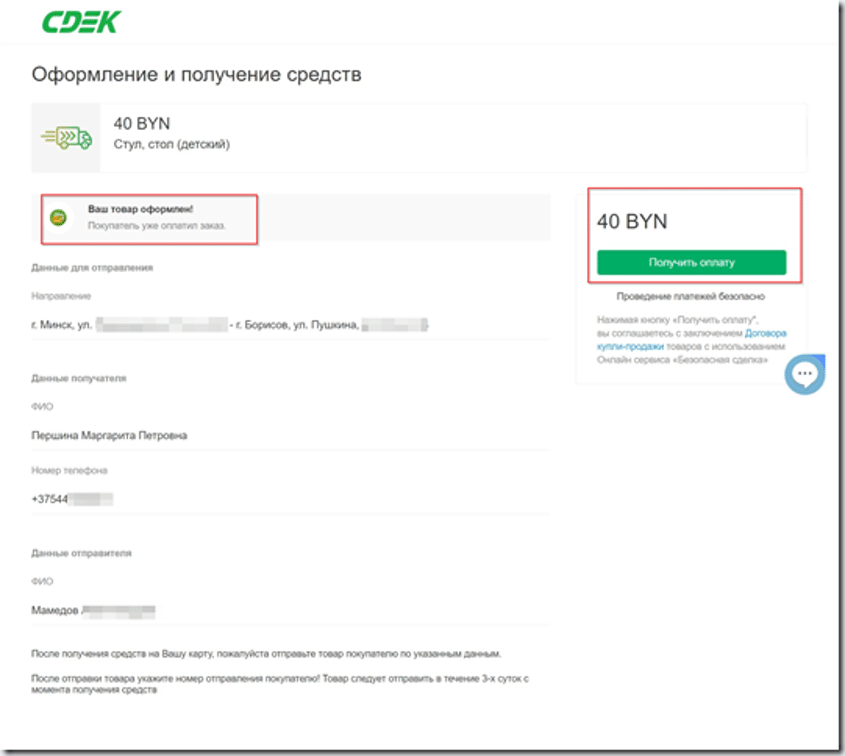
Red Flags Start to Emerge
The URL she provided was https://cdek.tel, but I knew the official Belarusian CDEK website was https://cdek.by. The presence of a padlock in the browser address bar, indicating a secure connection, momentarily reassured me.
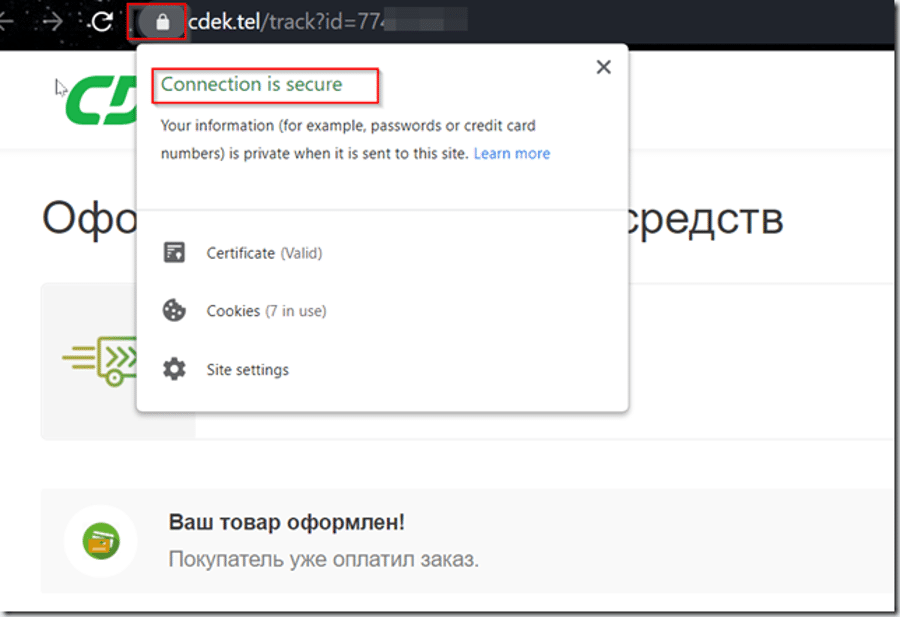
When I visited cdek.tel, it redirected to cdek.by, which made me second-guess my suspicions. Perhaps CDEK used a centralized domain for various countries?
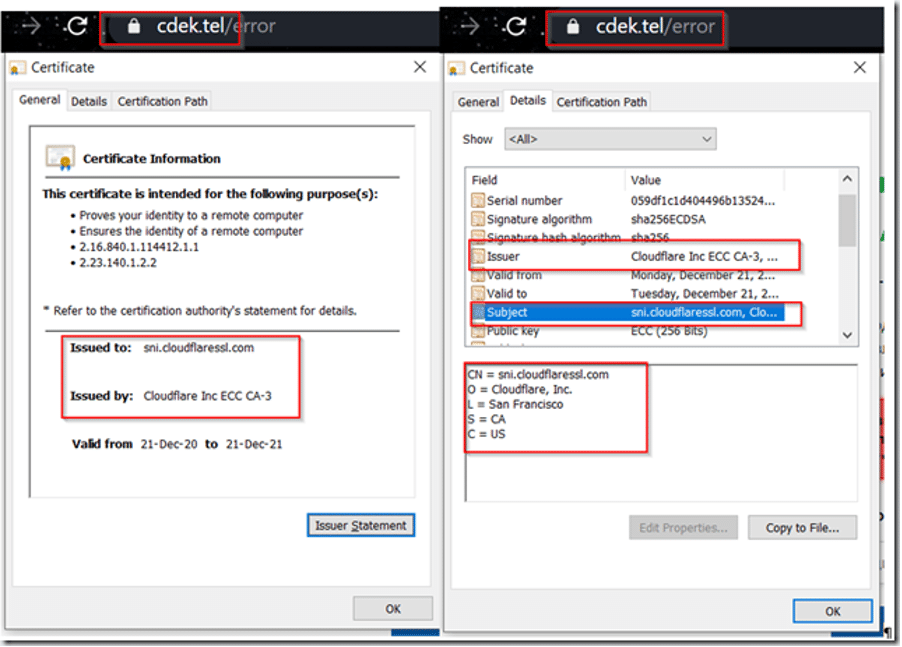
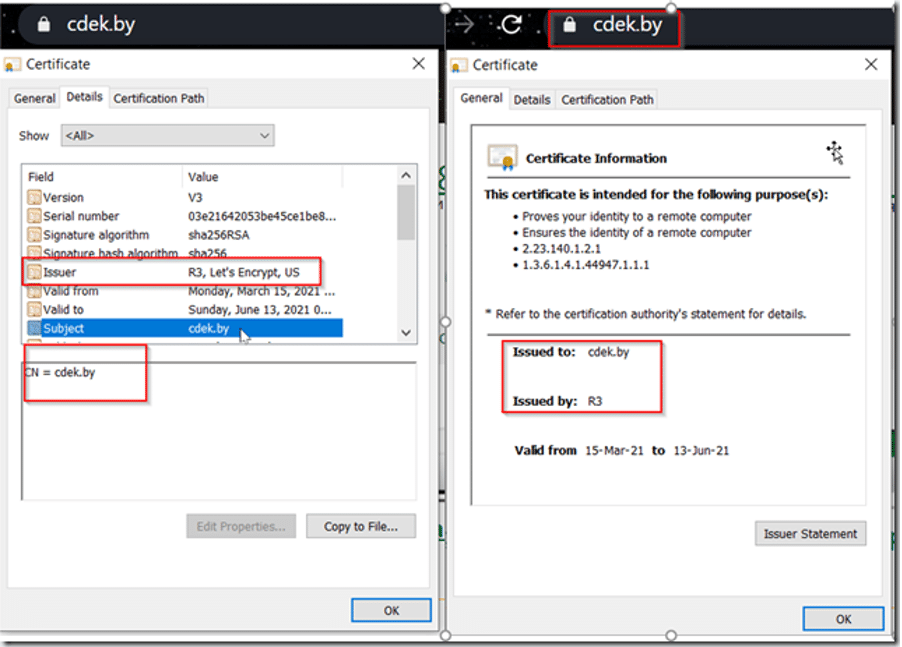
However, a deeper inspection revealed discrepancies:
– cdek.by had a free certificate from Let’s Encrypt,
– cdek.tel used a Cloudflare certificate associated with sni.cloudflaressl.com.
This raised a strong suspicion that cdek.tel was a spoofed site cloaked behind Cloudflare’s free CDN and SSL services—a common trick among phishing operators.
How the Scam Works Technically
The fraudulent cdek.tel domain hosted its DNS zone on Cloudflare. When visited, the browser connects to Cloudflare’s servers, which then proxy requests to the scammer’s hidden site—either via unencrypted HTTP (Flexible SSL) or encrypted HTTPS (Full SSL).
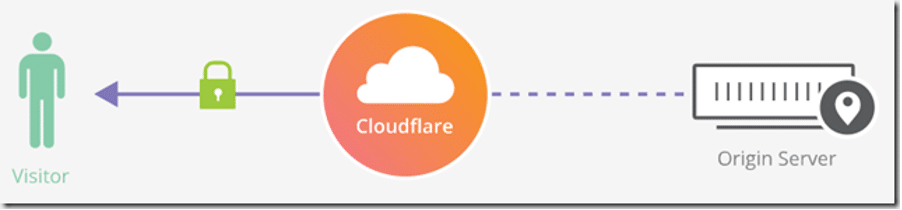
The user cannot determine the real server’s security level since Cloudflare handles all visible encryption. This setup is often used to obscure phishing operations.
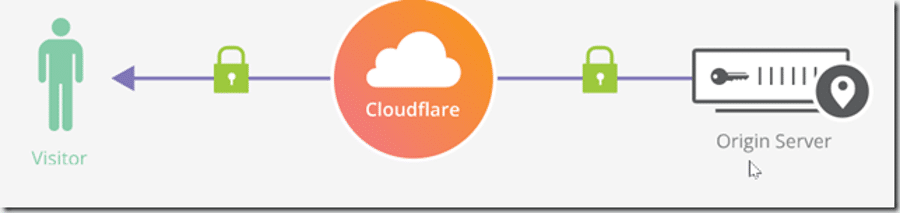
Further details are available on https://www.cloudflare.com/ssl/.
The Trap Springs
Curious, I clicked on the link to “receive payment.” A few alarming signs immediately appeared:
– The form asked for my CVC number—something completely unnecessary to receive money.
– The site’s chat feature displayed nonsensical characters when clicked.

Despite already being suspicious, I decided to go further by inputting fake card details. I clicked “Get,” supposedly to receive 40 rubles.
What followed was outright deception: the site asked for my card balance, citing a bogus security check—an obvious attempt to determine how much money they could drain from the card.
Finally, they tried to bypass 3-D Secure, a system used by banks for verifying transactions via SMS. The scam page mimicked a payment verification page (cdek.tel/3ds) and prompted me to enter a code that would typically be sent via SMS during a real transaction.
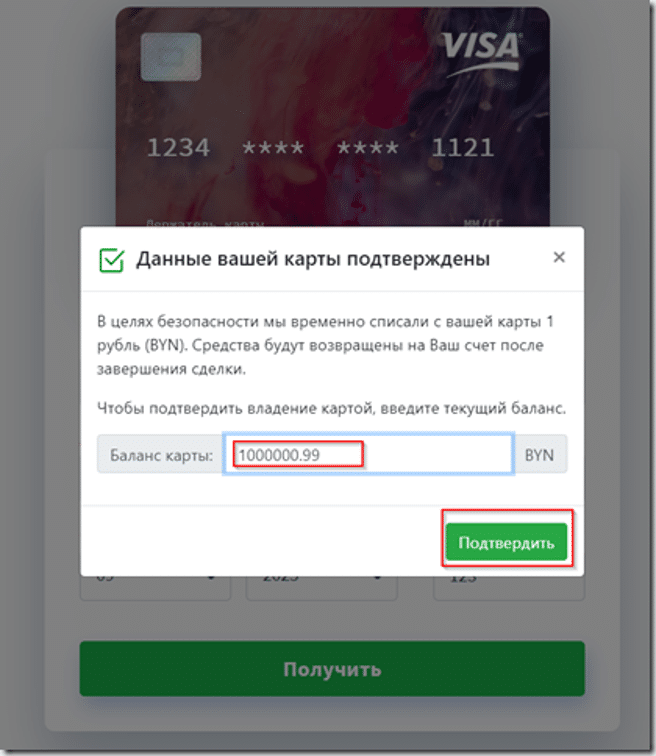

Had I entered an actual code, the fraudsters would have had everything they needed to empty my bank account—card number, CVC, billing address, and SMS verification.

Lessons Learned
Even after submitting false details, the fake site always returned an error page, no matter what input was given. A deeper network analysis (which I unfortunately didn’t save) would have revealed even more.
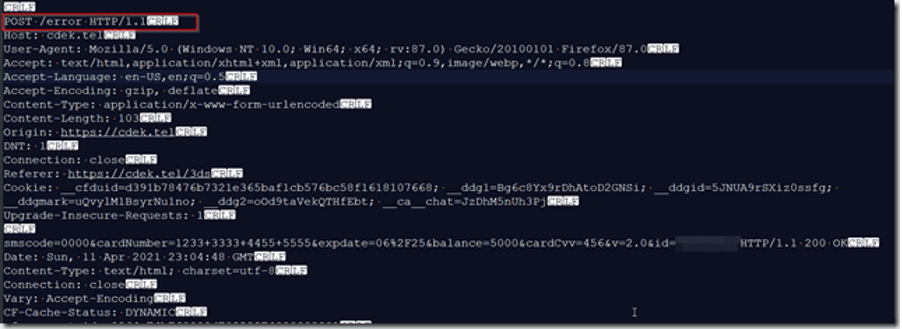
To sum up: The scammers impersonate a legitimate buyer and lure you into providing sensitive financial information via a counterfeit website. Once armed with your card details, they attempt unauthorized transactions under the guise of confirming payment.
How to Stay Safe
1. Question unexpected messages about deliveries, especially those requesting personal or financial information.
2. Verify independently—don’t trust links or information sent by strangers.
3. Use official channels—if unsure, visit the company’s official website or call them directly.
4. Never share your card’s CVC or SMS codes—these are meant for confirming payments, not receiving them.
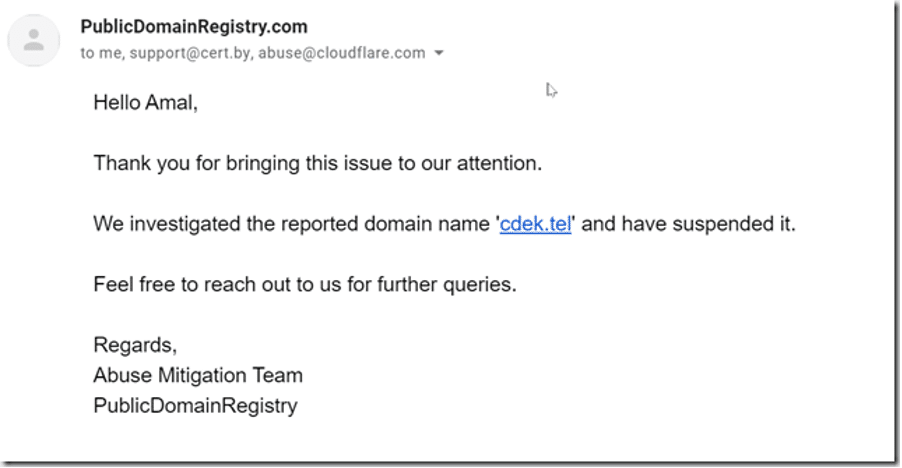
In my case, I reported the fraudulent domain to Cloudflare, CERT.by, and Publicdomainregistry. Thankfully, the domain cdek[.]tel was taken down within 24 hours.
Final Thoughts
The internet is rife with scams that are growing increasingly sophisticated. While tech-savvy users might recognize the signs, others may easily fall victim. Stay alert, scrutinize unfamiliar links, and protect your sensitive data. If something feels off—trust your instincts.
Thank you for reading. Stay safe online.
