With its rising popularity and value, cryptocurrency attracts the attention of cybercriminals. One of the most common methods these criminals use to steal cryptocurrencies is through malware, yet there are different ways they can do it. Let’s explore four common types of crypto malware.
Crypto Wallet Data Stealers
Crypto wallet data stealers are malicious programs that try to steal important information like private keys and seed phrases from cryptocurrency wallets on infected computers. These programs use tricks like process injection, keylogging, and file system scanning to find and take the sensitive information.
The stolen information is then sent to a remote server controlled by the attacker to be used later for theft. In most cases, such malware also features other capabilities, such as stealing the victim’s account credentials and sensitive data.
Example: RisePro
RisePro is a remote access trojan with an extensive set of capabilities, including crypto wallet stealing. It can exfiltrate crypto wallet data of many browser and desktop wallets, including MetaMask and Exodus.
To expose crypto malware like RisePro, we can use the ANY.RUN sandbox. This cloud service makes it possible to analyze suspicious files and URLs in a safe virtual environment. The sandbox automatically detects threats and malicious activities, as well as provides the user with complete interactive control over the process.
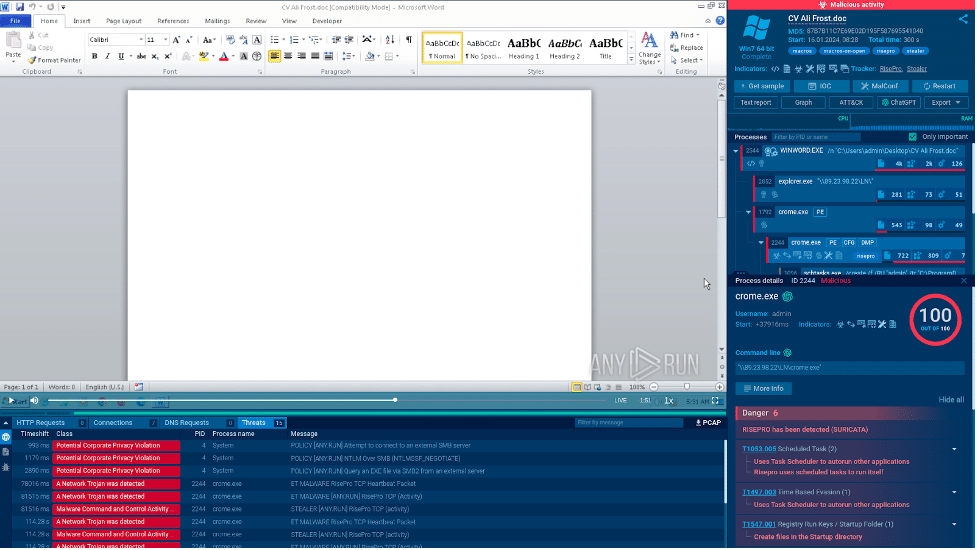
See this sandbox analysis of a RisePro sample.
Here, a .doc file with a built-in macro leads to the downloading and execution of the malware on the system. By proactively uploading such documents to the sandbox, you can avoid falling victim to an infection and losing your cryptocurrency.
Here, a .doc file with a built-in macro leads to the downloading and execution of the malware on the system. By proactively uploading such documents to the sandbox, you can avoid falling victim to an infection and losing your cryptocurrency.
Crypto Ransomware
Crypto ransomware encrypts files on a hacked computer using complex algorithms. After the files are encrypted, the malware usually shows a message demanding a ransom payment in cryptocurrency to get the decryption key. Some advanced ransomware programs use a combination of symmetric and asymmetric encryption for stronger security.
These threats may also steal sensitive information before or during encryption. To make sure they remain on the system, ransomware programs may create backdoors, change system settings, or use privilege escalation techniques.
Example: LockBit
LockBit is a prime example of a ransomware that demands payments in cryptocurrency. This threat uses double extortion, which means that victims are asked to pay for file decryption and to stop their stolen data from being published.
Check out this analysis of LockBit.
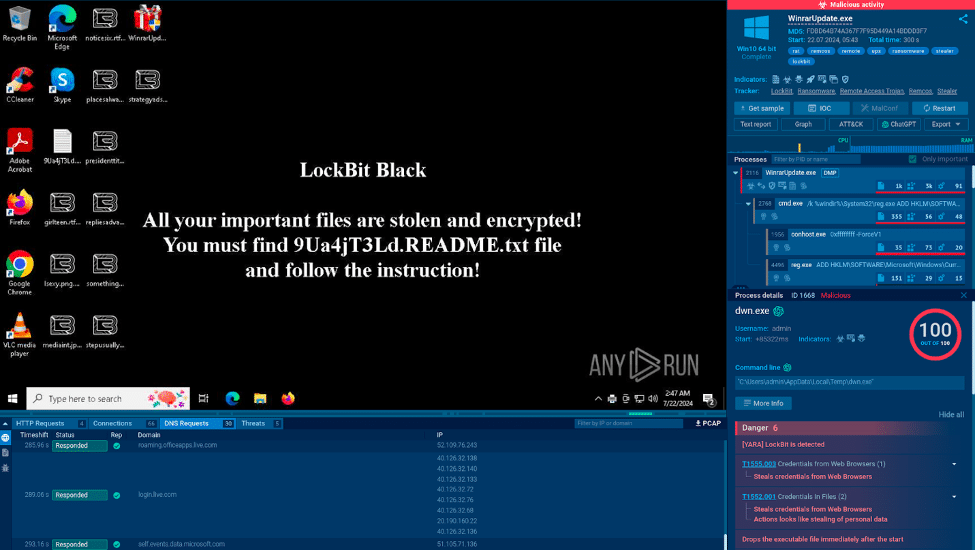
The malware in this case is distributed as a fake WinRAR update. As soon as it is detonated in the sandbox, LockBit starts encrypting files and changes the desktop wallpaper telling the user to open a Readme file to access further instructions.
Clipper Malware
Clipper malware is designed to intercept and manipulate clipboard data, targeting cryptocurrency transactions. It uses clipboard monitoring mechanisms to identify wallet addresses copied by the user. After detection, the malware replaces the legitimate recipient address with a cryptocurrency wallet address controlled by the attacker. This redirects the funds to the attacker’s account without the victim’s knowledge.
Example: Laplas Clipper
LaplasClipper is a malware that can create different types of cryptocurrency addresses, including Bitcoin. It can generate addresses with a prefix or postfix, giving criminals more control over how the fake addresses look. The software can replace addresses in over 20 popular crypto wallets and can be managed through a web-based interface.
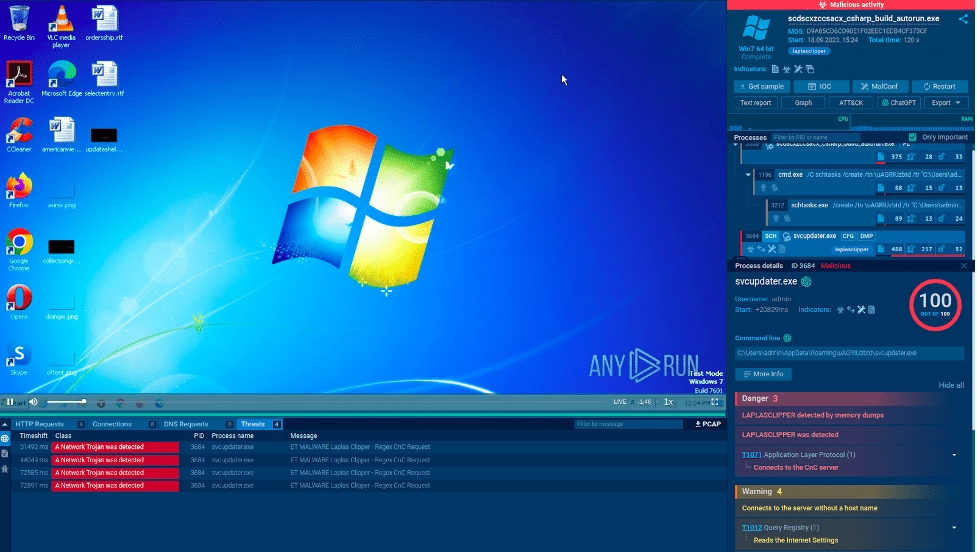
Here is a Laplas Clipper sample run in the ANY.RUN sandbox.
The service lists all the malicious activities performed by the malware, including its attempt to connect to the server controlled by the attackers.
Cryptojacking
Cryptojacking software is malicious code that secretly utilizes a user’s computer processing power to mine cryptocurrency without the owner’s knowledge or permission. This malware runs mining algorithms in the background, earning cryptocurrency for the attacker.
To hide its activities, cryptojacking software often uses tricks like process obfuscation, resource optimization, and network traffic masking.
Example: XMRig
XMRig is an open-source program that uses computer processing power to cryptocurrency. It works with both CPUs and GPUs. While it’s legal for personal use, it’s often misused by attackers as a cryptojacking tool to secretly mine cryptocurrency using other people’s computers without their permission.
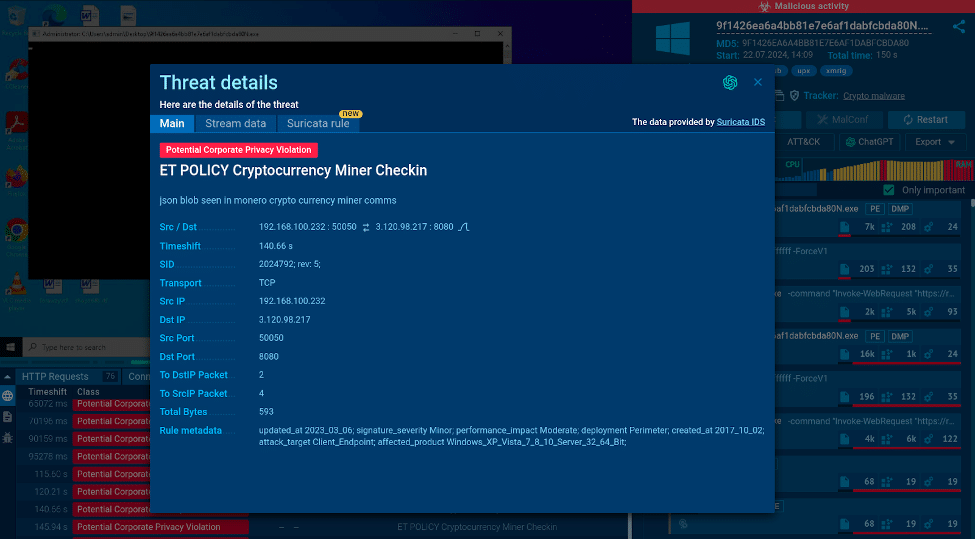
In this example, you can see XMRig being used for mining the Monero cryptocurrency.
In many cases, attackers often deceive users into installing such samples, gaining access to all the mined crypto.
Conclusion
Understanding crypto threats and taking necessary precautions can significantly reduce the risk of falling victim to such attacks. Always keep your system updated and always upload suspicious files and links to a free malware sandbox like ANY.RUN.
Use your business email to sign up for a free ANY.RUN account!