Academic institutions that include external training programs in their curricula have several advantages over those that don’t. Integrating a course from professionals into the learning process is arguably the easiest way to fill the gap between education and industry. Security Training Lab by ANY.RUN, a provider of malware analysis and threat intelligence solutions, aims to help universities achieve just that.
Security Training Lab by malware analysis experts
This course is based on real-world experience of professionals: ANY.RUN is an acclaimed company that has been tackling cyber threats since 2016. It offers a range of products for security teams at companies and organizations.
Security Training Lab helps future malware analysts upgrade their skillset and prepares them for joining the ranks of cybersecurity experts.
Integrating this practice-based course into the curriculum means that students will get to receive hands-on experience of working with real-world issues, while lecturers can monitor and manage their tasks and performance on the educational platform.
It’s a win-win situation, since the course complies with the needs of both educational institutions and relevant requirements of the industry. It can easily become a part of your learning management system.
Boost the learning process at your university with a practice-based course by ANY.RUN
What’s on the program
During the studies, the participants of the course will gain practical and theoretical knowledge in malware analysis. This includes static and dynamic analysis skills, as well as insights into tactics and techniques used by malicious files to avoid detection.
Security Training Lab consists of 30 hours of academic content, such as interactive tasks, written materials, videos, and tests for performance monitoring.
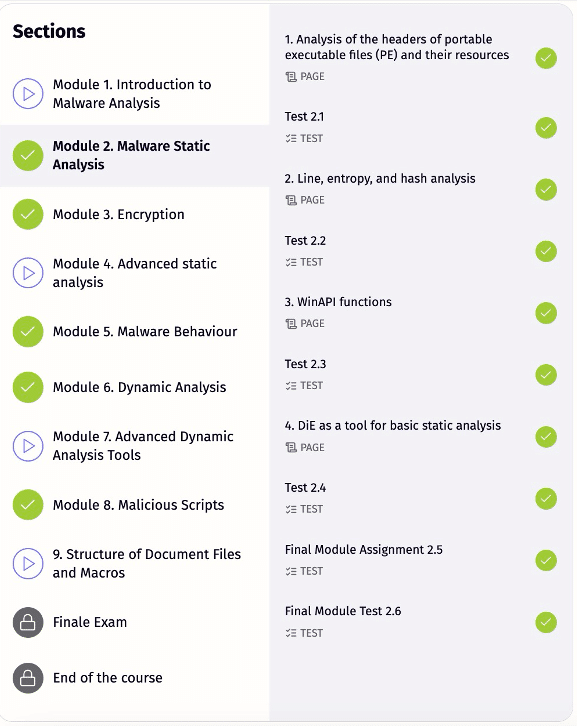
The list of modules at Security Training Lab
Additionally, both students and lecturers will be granted full access to ANY.RUN’s Interactive Sandbox for malware analysis, a cutting-edge tool used by security teams at companies across continents and industries. As part of sandbox practice, students will gain comprehensive understanding of malware’s behavior in an accessible way.
By exploring real-world threat samples and completing practical tasks, the participants will learn to investigate malicious files in detail and expand their expertise with up-to-date information on current cyber threats.

One of the task descriptions at Security Training Lab
Additionally, the students will get access to a private Discord community to exchange experience, gain more insights, and follow cybersecurity news. Upon graduation, they will receive a LinkedIn certificate and a discount for ANY.RUN’s services.
Conclusion
Security Training Lab is available for both educational institutions and individual specialists who want to upgrade their skillset and start to use cutting-edge malware analysis tools.