Basic Roles in Cyber Security
As beginners in the field of cyber security, people need to choose a path from one of these:
- Offensive Security
- Defensive Security
- Cyber Security Auditors
Offensive Security
The term “Red Team” refers to offensive security. Penetration testers who work as red teamers ethically try to hack a firm they are paid to hack and then present them with a report on what they found as well as a potential solution to repair it. Red team is about more than just testing. A proper red teaming operation would cover every stage of the hacking process, from phishing to developing malware for the targeted firm. The main goal is to secure the company from the perspective of a real-life hacker.
Defensive Security
It is a sort of security that tries to defend an organization in every situation. It starts from network analysis and progresses towards securing the network infrastructure by establishing a security plan to ensure the success of any security controls implemented. Defensive side is mostly related to watching and analysing the network 24/7 for possible threats and mitigate them accordingly.
Auditors
Cybersecurity auditors collaborate with businesses and organizations to conduct comprehensive audits of online security systems, which often involve the following:
- A comprehensive report on current cybersecurity systems.
- Analyze to see if the systems are running efficiently and effectively.
Auditors make sure that the implemented security controls are working efficiently.
Hackingloops has additional details if you want to learn about entry level jobs in cyber security.
Trending Cyber Security Jobs in 2021-2022
Although there can be many roles in the field of cyber security, but following are the ones that cover most of the job descriptions
Information security analysts
The most fundamental role in cyber security is that of an information security analyst. Security Operations Centers, or SOCs, are where most information security analysts work. SOC analysts are the people that monitor the target company’s network traffic to check whether any malicious events are happening. These analysts focus on network security rules and configurations. Based on their experience, L1, L2, and L3 SOC analysts are the three (3) jobs in Security Operations Centers. In short, responsibilities of SOC analysts are as follows:
- Monitoring security breaches on the network on targeted organization
- Investigating, documenting and reporting the security breaches
- Finding latest trends in cyber security and research on it
- Developing security techniques to aid their organization’s security
Red Teamers
On the attacking side, red teamers are the most sought after players. However, it should be noted that red teamers are not the same as penetration testers. A penetration tester merely tries to breach the system in an ethical manner with limited resources, but a red teamer does significantly more. Red teamers exploit real-world circumstances to uncover system flaws that a penetration tester would miss. Red teamers engage in a variety of activities, including the following:
- Phishing Attacks on the company personnel to check the security awareness of employees and to gain access to the company’s internal infrastructure
- Checking the company’s public resources for vulnerabilities
- Using online and public resources to exploit the weaknesses in the system
- Writing malware specifically for the network architecture of the targeted organization
- Implementing plans to exploit the physical security weaknesses
- Documenting the findings and sharing them with the clients
Infact, a red teamer would go for any option that can be used to harm the organization but ethically.
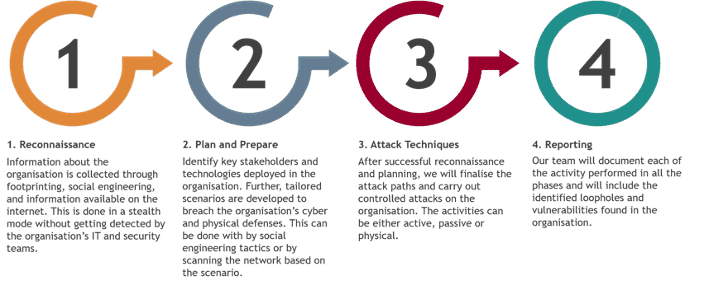
DFIR Guys
The area of digital forensics and incident response (DFIR) is concerned with the detection, investigation, and remediation of cyberattacks. These guys are the professionals who are called upon after an incident happens to perform analysis on the hackers’ activities. To remedy the breach and avoid a recurrence, forensics entails a detailed study of the data to acquire a complete knowledge of the incident. The actions conducted immediately after a security compromise, attack, or breach are known as incident response. Incident reponse works on 6 basic principals:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned

Malware Analysts
The job of a malware analyst is to utilize his/ her experience to determine the capabilities of malware and its ability to work. A malware analyst has to be a trained engineer who could easily reverse engineer the malware to know its functionality. A good malware analyst needs to know the following atleast:
- Knowledge of famous operatiof systems like KALI, Ubuntu, Windows platforms like 10 and 11.
- Knowledge of famous programminglanguages like python, C++, C#, Assembly etc.
- Tools that can ebe used for a basic malware analysis e.g. IDA Pro, OllyDbg, RegShot etc.
Consultants & Trainers
Cyber security consultants and trainers are important for keeping the resources of the company aware of the updated threats. Consultants and trainers perform a key role in the world of hacking. Many companies hire their trainers and some hire 3rd party trainers to inform their employees about the threats. Consultants and trainers can be used in the following areas:
- A trainer can be utilized to teach the developers about developing secure applications by following Secure Coding Practices.
- A trainer can develop practice labs for the employees of the company where they can get hands-on experience about the latest threats.
- Not only training the employees, but a consultant can also help in finding solutions to problems that a company faces in their daily life operations e.g. how to block the traffic that is causing DDoS attack on the company’s network.
