Phishing emails are getting sneakier by the day and it’s not always the message itself that does the damage. Often, the real threat hides in the attachment.
Cybercriminals use common file formats to trick users into opening malware-laced content. These files often look harmless and familiar. But behind the scenes, they’re running code, stealing credentials, or redirecting victims to fake login pages.
Here are three types of email attachments you should think twice before opening.
1. Archive Files: A Compressed Threat
Compressed files like .zip, .rar, or .7z are widely used for sharing multiple files in one neat package. That’s exactly why attackers love them too. These archives can sneak past email filters, often disguising malware as invoices, job applications, or shipping details.
Inside, you’ll find a file that looks normal but once opened, it can execute dangerous code without you realizing it. These attachments don’t raise alarms on their own, and there’s rarely any visible clue that something has gone wrong.
The good news is that these types of threats are easy to catch if you open them in a secure sandbox environment. A sandbox lets you run suspicious files in isolation, so even if they’re malicious, they can’t harm your actual system.
In real-world example, we analyzed a phishing email carrying a malicious RAR archive. Running it in the sandbox gave us an instant verdict: it’s malicious.
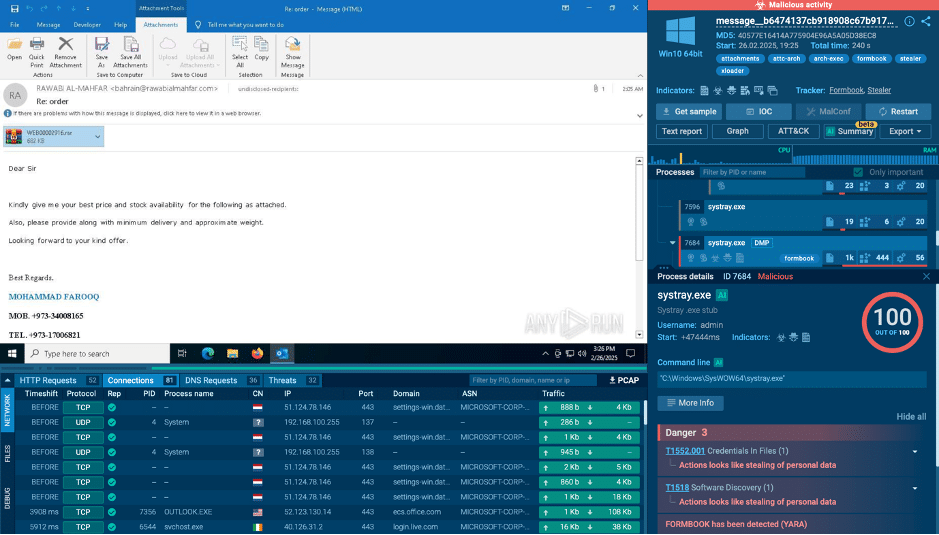
Phishing email with malicious archive analyzed inside ANY.RUN’s secure sandbox
The archive contains Formbook, an infostealer that targets saved passwords, clipboard content, keystrokes, and even screenshots. It’s known for quickly connecting to a command-and-control server, exfiltrating data in the background while the victim remains unaware.
Tip: If you receive an unexpected archive, don’t open it directly. Instead, test it safely in a sandbox to see what’s really going on.
| See what that file is really doing before it puts your system at risk. Join ANY.RUN now |
2. HTML Files: Looks Like a Page, Acts Like a Trap
HTML attachments might not raise eyebrows. After all, they’re just web pages, right? But that’s exactly what makes them risky. These files can open directly in your browser, and with some clever coding, they can imitate legitimate websites almost perfectly.
Attackers often use HTML attachments to craft phishing forms that look like login portals. Once you enter your credentials, they’re silently sent to the attacker; no malware download required.
For instance, in this ANY.RUN analysis session, we see an email claiming there was a missed call and an audio note attached. The note is actually an .html file. The email urges the recipient to open and “listen” to the audio, tempting, right?
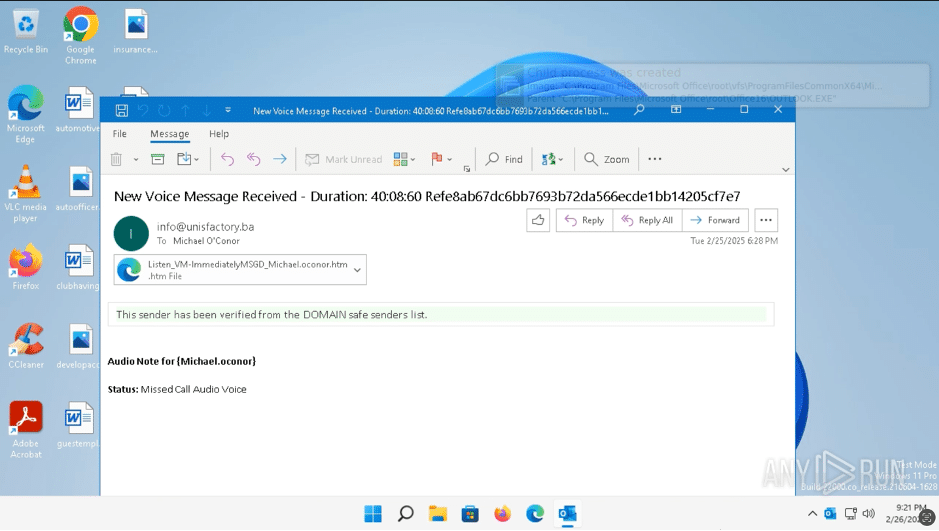
Malicious HTML file opened inside sandbox
But once the file is opened, it redirects to a malicious webpage, which then forwards the victim to a fake Microsoft Office login page. That’s where the trap is set. If someone enters their login info, it goes straight to the attacker’s hands.
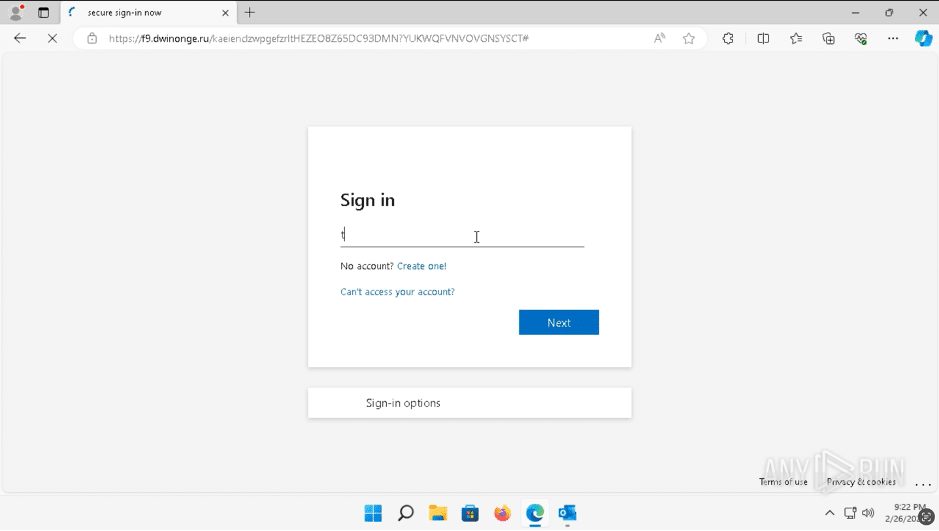
Fake Microsoft page detected by ANY.RUN sandbox
Tip: Treat unexpected HTML attachments with caution. While analyzing, pay close attention to the page name or URL that loads inside the sandbox. If it contains a string of random or suspicious characters, there’s a high chance it’s malicious and generated to evade detection.
3. PDFs More: Than Just a Document
PDFs are one of the most trusted file formats out there. We open them without thinking, whether it’s a receipt, a report, or an invoice. But that trust is exactly what makes them so effective in phishing campaigns.
Attackers can embed dangerous links, hidden scripts, or even files within PDFs that quietly redirect users to malicious websites or download additional payloads. Since many of these files look clean and professional, they often slip past both users and traditional detection tools.
In this real example, the PDF contains a link that appears to reference a graphic extension.
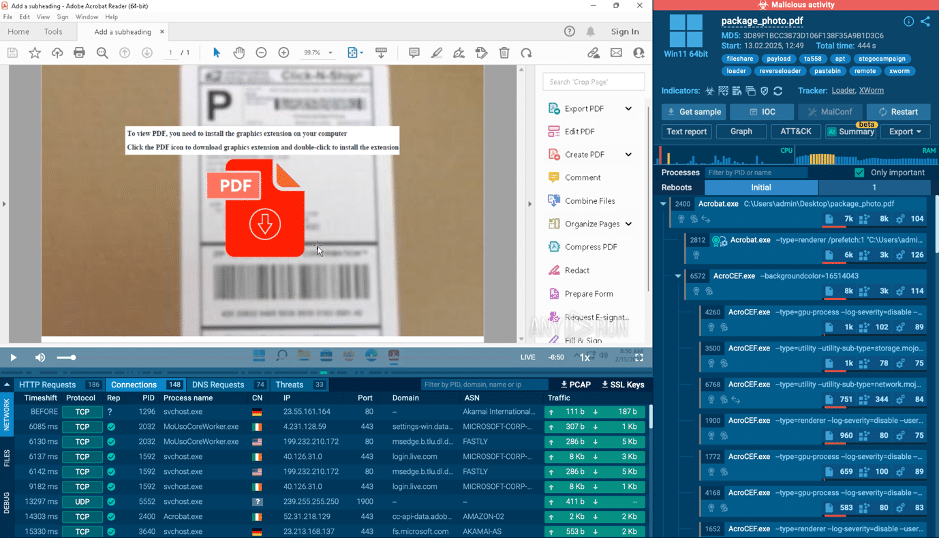
Malicious PDF file analyzed inside a secure ANY.RUN sandbox
However, clicking it triggers a chain of actions that downloads an image file containing embedded malware. Yes, you read that right; the malware is hiding inside an image.
This is a multi-layered attack that uses obfuscation, misdirection, and payload delivery through an unexpected medium. Complex tactics like these make manual detection extremely difficult.
However, tools like ANY.RUN’s interactive sandbox make it easy to follow the entire process in real time. You can see how the PDF behaves, what processes it starts, and even spot the image file that secretly contains the malicious payload.
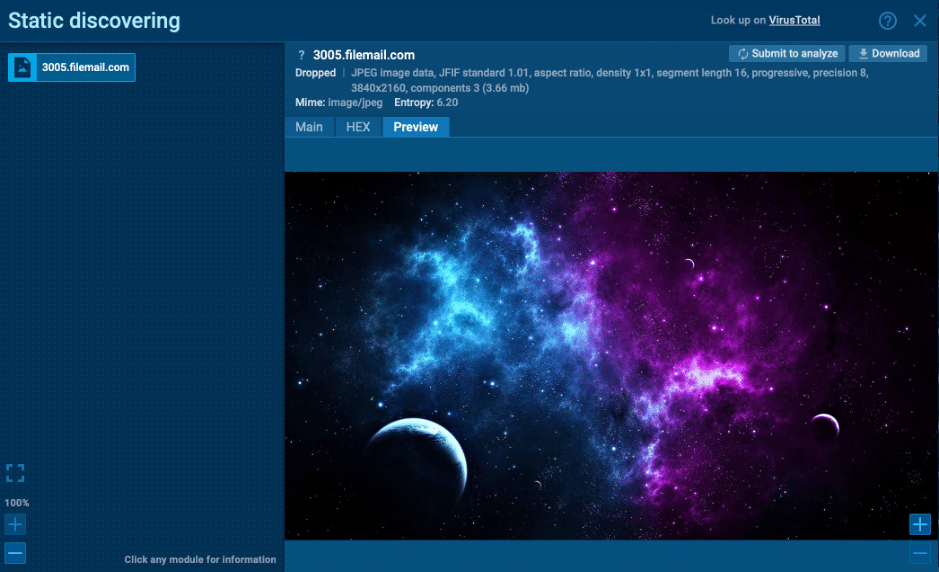
Image with a malicious payload detected
Tip: If a PDF urges you to click a link or open a file, pause. Even a simple-looking document can trigger a complex attack. When in doubt, check it in a sandbox first.
How to Stay Safe
Phishing attachments can be tricky, but a few simple habits can help you stay ahead of the game:
- Inspect links carefully: If a link looks suspicious or contains a string of random characters, don’t click.
- Be cautious with unexpected file types: Especially archives, PDFs, and HTML files from unknown senders.
- Avoid clicking buttons or links in documents: Even if they look legit, they might redirect you to phishing pages.
- Open suspicious files in a sandbox first: It’s the safest way to check what’s really inside.
What’s Hiding in That File? Find Out Without Risking Your System
You don’t have to be a malware analyst to spot a threat. With ANY.RUN’s interactive sandbox, you can upload and test suspicious files in real time, see every process unfold, and get a clear verdict in less than 40 seconds, without putting your system in danger.
Register now and start analyzing in a secure environment!
