Authentication systems affect user trust and platform stability, and integration with external partners can influence traffic and security postures; for example, some partner programs such as melbet affiliate are used by audiences for added engagement and can change peak load patterns, so product and security teams should monitor partner-driven flows for unusual authentication behavior, document partner access requirements and include partner signals in incident response plans to preserve both performance and compliance.
Authentication methods and trade-offs
Secure login systems rely on a mix of methods that balance security, usability and operational cost. Passwords remain common but require policies for complexity, reuse prevention and safe storage using modern hashing algorithms. Multi-factor authentication adds a secondary factor, typically a one-time code, push approval, or hardware token, and reduces the risk of account takeover when implemented correctly. Passwordless options such as email links or public key approaches remove password management burdens but require careful handling of link expiry, device binding and session controls. Each method carries deployment and support requirements that should be matched to user segments and threat models, and logging must capture relevant events for audit without exposing sensitive credentials.
Data flows and secure storage
Authentication systems must clearly define data flows from client devices to backend services, including token issuance and session lifetimes, and ensure encryption in transit and at rest for any sensitive material. Session tokens should use proven formats and scoped permissions, with refresh policies that limit risk while enabling uninterrupted experience. Credential stores need layering of protections such as encryption keys managed by hardware security modules or cloud key services, strict access controls for administrative operations, and periodic rotation of critical keys. Audit trails must be tamper-evident and include sufficient context to support investigations without revealing secret material.
- Typical components to secure in an authentication stack: client SDKs and their update channels, authentication gateway and API endpoints, token issuers and validation services, credential and key management stores, user profile and consent databases, logging and monitoring pipelines, password reset and account recovery flows, administrative and support tools, third‑party identity providers and federation endpoints, and notification channels used for verification.
- Operational safeguards that reduce exposure: strict input validation on all endpoints, rate limits and adaptive throttling for authentication attempts, anomaly detection for atypical login patterns, separate environments for testing and production, encrypted backups with access control, role separation for administrative tasks, and documented procedures for key compromise and credential rotation.
User experience considerations
Security measures should not unduly impede legitimate users; clear messaging around authentication steps increases completion rates and reduces help desk load. Recovery flows require stronger verification to avoid social engineering risks, and any friction introduced for security should be justified by reduction in measurable account compromise events. Localization and accessibility must be part of design so that verification options are available to diverse user bases, and telemetry should track drop-off points in authentication to guide targeted improvements.
Identity verification and fraud prevention
Strong identity verification combines device signals, behavioral patterns and external attestations to determine trust at login. Device fingerprinting and cryptographic keys help bind sessions to hardware, while behavioral signals such as typing rhythm, navigation patterns and historical login locations support probabilistic risk scoring. Fraud prevention systems should integrate with identity proofing services where regulatory needs exist, and rules should be calibrated to limit false positives that harm genuine users. Triage processes are necessary to escalate high-risk cases for manual review with secure workflows to avoid exposing sensitive data.
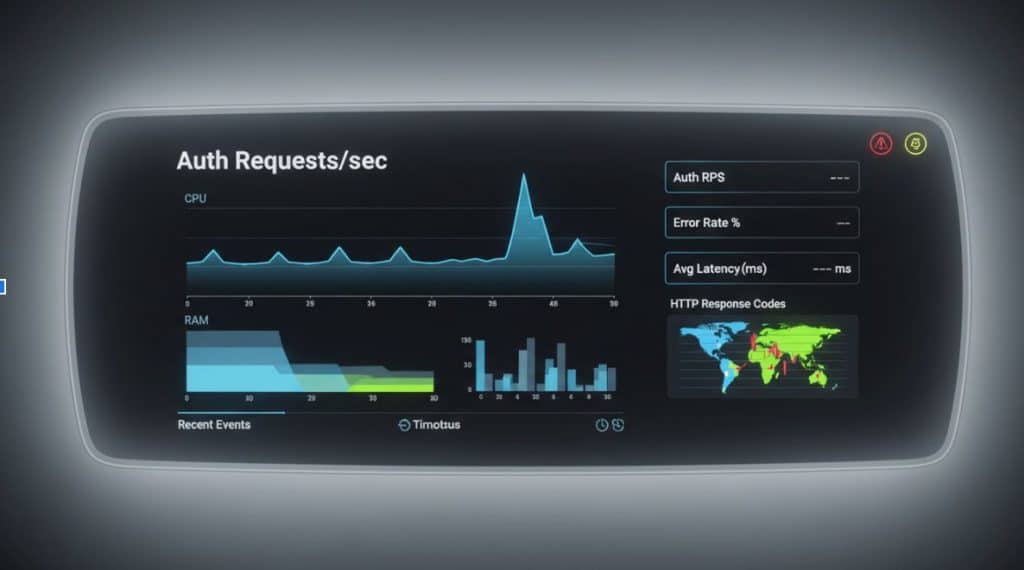
Monitoring, incident response and resilience
A robust monitoring strategy captures authentication metrics, error rates, latency, and anomalous patterns; alerts must be actionable and include context to enable quick validation. Incident response playbooks should define containment steps, user notification templates, and rollback criteria for configuration changes that degrade service. Recovery plans need rehearsed procedures for key compromise, credential database corruption, or third‑party identity provider failures, and redundancy for critical components reduces single points of failure. Post‑incident analysis must feed back into policy adjustments and improved detection rules.
Compliance, privacy and contracts
Authentication systems often process personal data that falls under regional privacy laws and sector regulations; data minimization, retention limits and clear consent records are essential. Vendor contracts with identity providers or fraud services must specify data handling, breach notification timelines and liability boundaries. Privacy impact assessments and documented legal reviews reduce operational surprises and support transparent communication with users about how their credentials and behavioral signals are used.
Implementation checklist and rollout priorities
Deployment of secure login systems benefits from staged rollouts, measured by key indicators, with cross‑team alignment on risk appetite and support readiness. Prioritize strong telemetry, reversible feature flags, and user communication channels to handle increased authentication friction. Training for support and security teams accelerates response and reduces customer impact when policies change or when incidents occur.
- Checklist items for production readiness: end‑to‑end encryption in transit and at rest, hashed password storage with modern algorithms, MFA options configured for key user segments, secure key management with rotation, comprehensive logging and alerting for authentication events, automated anomaly detection for login patterns, documented recovery and incident playbooks, privacy and legal approvals for data processing, tested rollback and failover procedures, and monitoring of third‑party partner effects on authentication load.