With cloud adoption skyrocketing and threat vectors on the rise, AWS security has become a topic of discussion in every IT boardroom. Yes, AWS is not just an IT checkbox anymore! As AWS adds new features and enforces tighter guardrails, an active, multi-layered approach is needed to protect workloads, data, and identities.
And AWS, the dominant cloud provider, supports all sorts of things from fintech to national healthcare initiatives. With great power, however, comes a rising storm of risk.
Whether you’re a CTO, a DevSecOps engineer, or a startup founder, the next 10 best practices will future-proof your cloud.
1. Implement Multi-Factor Authentication (MFA) for All Accounts
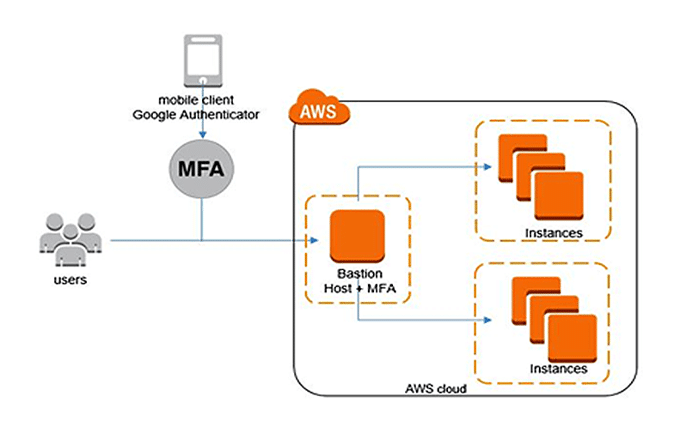
In 2025, the foundation of security is MFA. AWS now enforces MFA for all root accounts, and recommends hardware-backed FIDO2 devices for privileged IAM roles. A single compromised account can expose an entire cloud environment, making MFA a critical first line of defence.
Follow these steps to enable MFA:
- Use AWS Identity Center to implement MFA policies throughout the organization.
- Register multiple MFA devices for break-glass recovery.
- Check user accounts for MFA compliance with IAM Access Analyzer periodically.
2. Multi-Account Strategy and Zero Trust Architecture
AWS promotes a best practice to securely scale using a multi-account configuration. Workloads are separated by environment, such as production and staging, while keeping lateral movement possible once a breach occurs.
If a company is managing dozens to hundreds of AWS accounts, it becomes difficult to push out policies and governance consistently. That is why most of them use AWS staffing partners who focus on developing scalable security architecture against federated cloud environments.
Coupled with Zero Trust principles, where every request is verified, authenticated, and authorised, this architecture offers superior security.
The underlying principles of zero trust are:
- Use Verified Access for safe app-to-user authentication.
- Separate microservices using VPC Lattice, and employ Security Groups to restrict traffic.
- Use ABAC(Attribute-Based Access Control) to enforce more fine-grained access control.
3. Continuous Monitoring and Automatic Detection
Security is as much a matter of visibility as of control today. AWS offers a suite of detection tools that can (and should) be integrated across accounts. They include;
- AWS CloudTrail for API tracking
- Amazon GuardDuty for anomaly detection
- Security Hub for compliance benchmarking
- AWS Config for detecting configuration drift
The best practices are:
- Turn on GuardDuty for every account and every AWS region.
- Gather logs into one account with AWS Organizations.
- Automate remediation via EventBridge and Lambda functions.
4. Principle of Least Privilege over IAM
Over-permissioned IAM roles are probably the most common AWS misconfiguration. AWS enhanced IAM Access Analyzer in 2025 to detect unused permissions and warn on overly permissive policies.
Security groups should avoid using wildcard permissions (e.g., “*:*”) and instead define the required actions and resources. Security may be tightened further through regular audits, permission boundaries, and service control policies (SCPs).
Steps to follow the least privilege:
- Use group-based permissions and job roles rather than individual policies.
- To check for cross-account accessibility, configure Access Analyzer.
- Clear out unused accounts and rotate your IAM credentials.
5. Encrypt Everything And Manage Your Own Keys
Encryption at AWS is native, but management of your encryption approach turns good security into exceptional security. While AWS offers encryption by default for items like S3, EBS, and RDS, the use of Customer-Managed Keys in AWS Key Management System offers more control.
Misconfigured key policies or the absence of key control can lead to silent data exposure. So, what are the best practices for encryption?
- Utilize CMKs with auto-rotation every 12 months.
- Encrypt data in transit via TLS across all services.
- Enable logging for all key usage and attach tight IAM policies to key access.
6. Strengthen Your Network Layers with Multiple Guardrails
Network security remains important, especially for publicly accessible applications. AWS recommends a layered strategy:
- Segregate VPCs according to function and workload.
- Use AWS WAF and AWS Shield Advanced for DDoS protection.
- Use VPC Flow Logs and AWS Network Firewall to log and filter traffic.
The most significant 2025 trend is the use of threat intelligence feeds like MadPot in conjunction with AWS Network Firewall for filtering known malicious IPs at the edge. These pre-emptive filters significantly reduce the chances of botnets and DDoS attacks.
What to implement:
- Place public services behind CloudFront + WAF.
- Block all unused ports and restrict incoming traffic by CIDR blocks.
- Monitor lateral movement via VPC Flow Logs and anomaly notifications.
7. Automate system hardening and patch management
Unpatched containers and old AMIs remain the number one cause of cloud exploits. Auto-patching your process is the key to having a secure stack.
Features like AWS Systems Manager Patch Manager and AWS Inspector now support additional OS types, along with real-time vulnerability scanning.
The following is the security automation checklist:
- Regular scheduling of EC2, RDS, and container image patching is required.
- Run AWS Inspector on EC2, Lambda, and EKS workloads.
- Establish baseline configurations using Systems Manager and State Manager.
8. Shift Security Left in Your CI/CD Pipeline
With how DevOps has developed, having security built right into your development process now is a bare minimum.
AWS released Inspector Code Security in 2025, which scans pull requests for vulnerabilities. Combined with infrastructure-as-code scanning tools like Checkov and TFSec, it ensures misconfigurations are not deployed to production.
DevSecOps best practices are as follows:
- Include security checks in CodePipeline or GitHub Actions phases.
- Use STRIDE to create threat models during backlog grooming or sprint planning.
- Employ pre-merge security linting for Terraform or CloudFormation.
9. Create Incident Response Playbooks and Rehearse Them
No system is breach-proof. The way resilient businesses respond to security makes them stand out. AWS suggests developing automated playbooks for high-risk situations:
- Root account usage
- Privilege escalation
- Public S3 bucket detection
- Suspicious VPC port scans
Simulated events, such as tabletop exercises, allow teams to practice isolating assets, taking forensic snapshots, and communicating under stress.
So, how do you prepare?
- Store cleaned-up copies of the most important AMIs and Docker images.
- Automate security incident notifications using CloudWatch and EventBridge.
- Document and rehearse workflows for potential critical response scenarios.
10. Improve Detection with AI and Threat Intelligence
The future of cloud security lies in AI-powered machine learning. AWS already uses AI models through offerings like GuardDuty and Security Lake to detect behavioral anomalies in CloudTrail logs, DNS traffic, and VPC flow logs.
As per a recent study, reinforcement learning architectures have boosted the precision of threat detection to as much as 92% over rule-based systems. Even though not all organisations possess ML teams, adopting managed tools with AI bridges the gap.
Use AI responsibly:
- Leverage GuardDuty’s machine learning-driven anomaly notifications for real-time identification.
- Feed threat intelligence into firewall and WAF rules.
- Review machine-learning-driven information regularly with your security team.
Whether incident response configuration, multi-account governance configuration, or AI-workload hardening, seasoned AWS-certified engineers can help corporations better secure their operations without diverting internal resources.
Final Thoughts
AWS now has smarter and more intuitive security than ever. But best practices still require commitment to embrace. Top AWS security strategies would encompass enforced MFA and Zero Trust designs with real-time threat detection and patch automation in 2025 for proactive defense and agile response.
When done correctly and with the right knowledge, such approaches turn cloud from a potential liability into a strategically secured growth platform.
