When you choose a proxy service, whether it offers ISP, datacenter, or residential proxies, one fundamental question often arises: which protocol should you use, HTTP or SOCKS? But before you can answer that, you might wonder what a web proxy protocol actually is. In simple terms, it is the set of rules that governs how your client communicates with a proxy server and how that server forwards your requests to the internet. The type of protocol can impact connection stability, speed, and how your traffic appears to target websites.
Understanding these protocols and their differences is crucial for configuring your tools correctly and achieving your desired online results. This knowledge helps you make an informed choice that aligns with your specific technical needs. This article explains the core concepts, versions, and primary types of proxy protocols. It will provide a clear overview to help you navigate this essential aspect of proxy use, ensuring you have the foundational knowledge to proceed confidently.
What Is a Web Proxy Protocol?
A web proxy protocol is a standardized set of rules that defines how a connection is established between your device, a proxy server, and the final destination online. Think of it as a common language that allows these different points to communicate effectively. When you use a proxy, your internet traffic is routed through an intermediary server. The specific protocol you use dictates how your request is packaged, sent, and interpreted by this server before it reaches the target website.
This standardization solves a fundamental problem. Traditional proxy setups can cause the destination server to lose the original connection information, such as your real IP address. The introduction of a dedicated proxy protocol helps preserve this crucial client data as the request passes through the intermediary. This is vital for tasks that require accurate logging, geographic targeting, or security analysis, which ensures the backend systems receive the complete picture of the connection’s origin.
Different Versions of Proxy Protocols
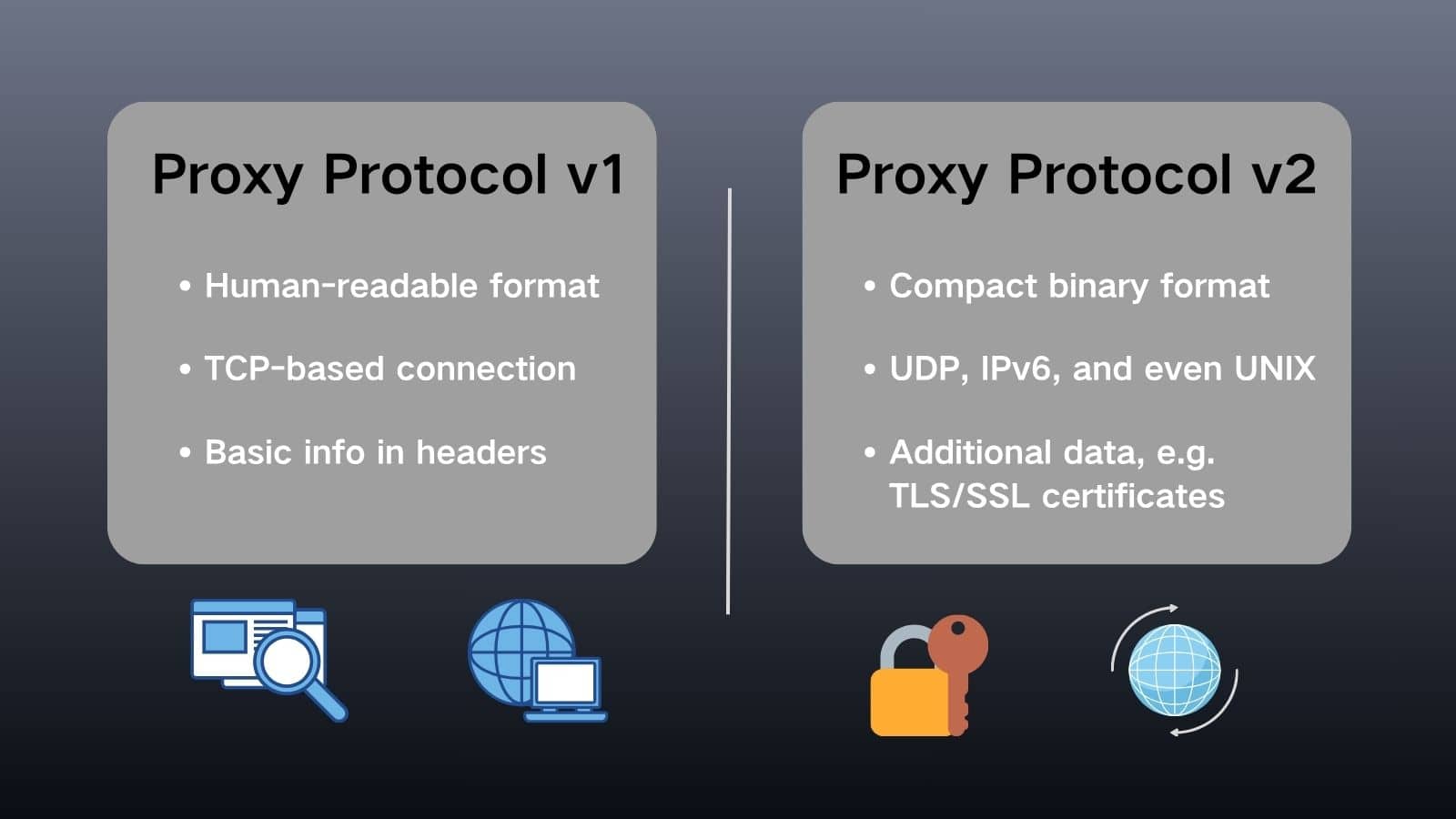
To address the need for preserving original connection information, specific versions of the proxy protocol were developed. The two main iterations are Proxy Protocol v1 and Proxy Protocol v2. These versions provide a standardized method for transmitting client data. The following sections will outline the key characteristics of each version.
Proxy Protocol Version 1
Proxy Protocol v1, the original version of this specification, was developed by HAProxy Technologies to preserve a client’s original connection information. This human-readable protocol works by adding a single line of plain text header at the very beginning of the TCP connection. This header starts with the “PROXY” keyword and communicates essential details like the client’s source IP address, destination IP, and port numbers.
The primary advantage of Proxy Protocol v1 is its simplicity. Being in a text format, it is straightforward for humans to read and for systems to parse, making initial implementation and debugging easier. However, this text-based design also defines its limitations. It is not suitable for binary protocols and is inherently less efficient. Furthermore, as the header is unencrypted, it must be used within a secure, trusted network path between the proxy and the final server to prevent potential data manipulation.
Proxy Protocol Version 2
As the binary successor to the text-based v1, Proxy Protocol v2 was designed to address the limitations of its predecessor by offering a more efficient and robust solution for transmitting original connection information. This version uses a compact binary header, which significantly reduces processing overhead.
A key characteristic of Proxy Protocol v2 is its expanded capability. It supports not only TCP but also UDP and UNIX stream sockets. Furthermore, its binary format allows it to reliably carry additional crucial data, such as IPv6 addresses and Transport Layer Security (TLS) connection attributes. This makes it more secure and less prone to parsing errors compared to the text-based v1. Due to these advantages, Proxy Protocol v2 is increasingly becoming the modern standard for preserving client information in complex network environments.
A Brief Comparison Between V1 and V2
Understanding the key differences between these two versions helps in selecting the right one for your infrastructure.
- Format and Performance: Proxy Protocol v1 uses a human-readable text header, which is simple but requires more processing power to parse. In contrast, Proxy Protocol v2 employs a compact binary format. This design makes v2 significantly more efficient for servers to process, reducing latency, especially under high-traffic conditions.
- Protocol Support: The text-based v1 is fundamentally designed for TCP-based connections like HTTP. Proxy protocol v2, however, has a broader scope with native support for UDP, IPv6, and even UNIX domain sockets, making it adaptable to a wider range of modern network applications.
- Data and Reliability: The v1 header contains basic connection information. The binary structure of v2 allows it to reliably carry additional data, such as TLS/SSL certificates, and is less susceptible to parsing errors or spoofing attacks, offering enhanced security and data integrity.
Main Types of Web Proxy Protocols
Beyond the versions of the proxy protocol itself, there are 3 fundamental types of proxies defined by their communication rules. These are the protocols you typically select when configuring your software. The most common web proxy protocol types each serve different purposes and offer unique advantages for various online tasks.
HTTP Proxy Protocol
The HTTP proxy is a widely used type designed primarily for handling web traffic. It operates at the application layer, meaning it understands and can interpret the content of HTTP and HTTPS requests. A key feature of this web proxy protocol is its ability to read and process the data being sent and received. This allows it to perform tasks like caching frequently accessed web pages to speed up loading times or filtering content based on predefined rules.
This protocol is commonly chosen for specific scenarios where its application-level awareness provides a direct benefit:
- Web Scraping and Data Aggregation: It is effective for extracting public data from websites, as it can handle web page requests and parse HTML content efficiently.
- Content Filtering and Access Control: Organizations often use it to enforce internet usage policies, blocking access to specific websites or types of content.
- Bypassing Geo-restrictions: It can be used to access region-locked web content by routing requests through a server in a permitted location.
- Ad Verification and Brand Safety: Companies use it to check how and where their online ads are displayed across different regions.
HTTPS Proxy Protocol
An HTTPS proxy, often called an SSL proxy, is fundamentally an HTTP proxy with a critical enhancement: the ability to handle encrypted HTTPS traffic. It acts as an intermediary for secure web requests, establishing a tunnel between the client and the target server. What matters is that it can manage the Transport Layer Security (TLS) encryption and decryption process, which allows it to securely forward requests without exposing the data content.
This focus on secure connections makes it suitable for several common applications:
- Secure Web Browsing: It is used to add a layer of security and privacy for general internet browsing, especially on untrusted networks, by ensuring all data remains encrypted.
- Accessing Financial or Sensitive Portals: It is ideal for tasks that involve logging into online banking, email, or any service where protecting login credentials and personal data is paramount.
- E-commerce Price Monitoring: Businesses use it to securely gather pricing and product information from competitor websites, as the encrypted connection helps mimic real user traffic and avoid detection.
- Secure Data Scraping: It is employed for extracting data from websites that require a secure HTTPS connection, ensuring the data transfer remains private and tamper-proof.
SOCKS Proxy Protocol
The SOCKS protocol operates at a lower level than HTTP proxies and functions as a general-purpose tunnel that relays traffic without interpreting it. The most common version, SOCKS5, supports various traffic types, including TCP and UDP, and offers authentication. Its primary advantage is high versatility, as it can handle diverse data streams beyond just web browsing, such as email, gaming, or file transfers. Many premium proxy providers, such as IPcook, support this protocol to offer users greater flexibility for complex networking tasks.
Common use cases for the SOCKS proxy include:
- Handling Multiple Traffic Types: It is ideal for applications that use different network protocols simultaneously, where an HTTP proxy would be insufficient.
- Peer-to-Peer (P2P) Activities: Its ability to relay UDP traffic makes it suitable for P2P file sharing and certain streaming applications.
- Bypassing Network Restrictions: It is effective for routing all traffic from a specific application through a proxy to circumvent firewalls.
- Online Gaming and Video Streaming: It can reduce lag and help bypass geo-blocks for gaming servers and streaming platforms that use non-web protocols.

Why Proxy Protocols Matter
The specific protocol you choose acts as the foundation for how your online interactions are managed. Selecting the right one is not just a technical detail; it is a strategic decision that impacts your operational success. The reasons below highlight their importance.
- Security and Anonymity: Protocols define how your original IP address is handled. A properly configured proxy protocol helps mask your real IP, enhancing your anonymity and protecting your identity from target servers.
- Data Integrity and Source Preservation: Using a dedicated proxy protocol ensures that the original connection information, like the client’s IP address, is accurately passed to the destination server. This is critical for logging, geo-targeting, and security analysis.
- Compatibility and Flexibility: Different tasks and software require different protocols. The right web proxy protocol ensures your tools, such as browsers, scrapers, or gaming clients, can connect and function without issues.
- Performance and Reliability: Efficient protocols, like Proxy Protocol v2, reduce connection overhead and latency. This leads to faster response times and more stable connections, which are vital for high-volume tasks like data scraping.
- Functional Capabilities: Some protocols enable advanced features. For instance, SOCKS5 can handle UDP traffic for gaming, while HTTPS proxies manage encrypted data, expanding the range of possible applications.
FAQs About Proxy Protocols
1. Which Proxy Protocol Is the Best?
There is no single “best” protocol, as the ideal choice depends entirely on your specific needs. Each web proxy protocol has distinct strengths and weaknesses. You should select a protocol based on your specific task, considering factors like required security level, traffic type, and the tools you are using.
2. What Are Proxy Protocol Headers?
Proxy protocol headers are packets of information added to the beginning of a connection that carry metadata about the original client request. Common examples in other contexts include headers like Via and X-Forwarded-For. Their primary purpose is to reliably transmit the client’s original IP address and other connection details to the destination server, which is crucial for logging and access control.
Final Thoughts
Understanding web proxy protocols is fundamental to leveraging proxy technology effectively. We have explored the different versions, from Proxy Protocol v1 to the more advanced Proxy Protocol v2, and examined the main types like HTTP, HTTPS, and SOCKS. Each serves a distinct purpose, and your choice should align with your specific requirements for security, compatibility, and performance. In short, a solid grasp of these protocols enables you to configure your tools effectively and achieve good results in your online activities.